서비스는 기본적으로 SYSTEM 계정이다.
이 서비스가 어떠한 프로세스 (exe)를 실행시켜주게 되면,
계정이나 권한도 그대로 승계받게되어, SYSTEM 계정으로 실행이 된다.
하지만 SYSTEM 계정의 Service는 기본적으로 UI를 지원하지 않는다.
UI를 지원하려면 USER계정으로 실행이 되어야 하는데,
이 때, 서비스에서는 특정 프로세스(exe)를 실행시켜줄 때, 단순히 Process.Start()를 하게되면
SYSTEM 계정으로 실행되게 되고,....
웹상에 흔히 돌아디는 아래코드를 이용해서 USER권한으로 실행하게 된다.
(advapi32.dll 의 CreateProcessAsUser 함수를 이용하는 방법)
아래는 샘플들
public class ApplicationLoader
{
#region Structures
[StructLayout(LayoutKind.Sequential)]
public struct SECURITY_ATTRIBUTES
{
public int Length;
public IntPtr lpSecurityDescriptor;
public bool bInheritHandle;
}
[StructLayout(LayoutKind.Sequential)]
public struct STARTUPINFO
{
public int cb;
public String lpReserved;
public String lpDesktop;
public String lpTitle;
public uint dwX;
public uint dwY;
public uint dwXSize;
public uint dwYSize;
public uint dwXCountChars;
public uint dwYCountChars;
public uint dwFillAttribute;
public uint dwFlags;
public short wShowWindow;
public short cbReserved2;
public IntPtr lpReserved2;
public IntPtr hStdInput;
public IntPtr hStdOutput;
public IntPtr hStdError;
}
[StructLayout(LayoutKind.Sequential)]
public struct PROCESS_INFORMATION
{
public IntPtr hProcess;
public IntPtr hThread;
public uint dwProcessId;
public uint dwThreadId;
}
#endregion
#region Enumerations
enum TOKEN_TYPE : int
{
TokenPrimary = 1,
TokenImpersonation = 2
}
enum SECURITY_IMPERSONATION_LEVEL : int
{
SecurityAnonymous = 0,
SecurityIdentification = 1,
SecurityImpersonation = 2,
SecurityDelegation = 3,
}
#endregion
#region Constants
public const int TOKEN_DUPLICATE = 0x0002;
public const uint MAXIMUM_ALLOWED = 0x2000000;
public const int CREATE_NEW_CONSOLE = 0x00000010;
public const int IDLE_PRIORITY_CLASS = 0x40;
public const int NORMAL_PRIORITY_CLASS = 0x20;
public const int HIGH_PRIORITY_CLASS = 0x80;
public const int REALTIME_PRIORITY_CLASS = 0x100;
#endregion
#region Win32 API Imports
[DllImport("kernel32.dll", SetLastError = true)]
private static extern bool CloseHandle(IntPtr hSnapshot);
[DllImport("kernel32.dll")]
static extern uint WTSGetActiveConsoleSessionId();
[DllImport("advapi32.dll", EntryPoint = "CreateProcessAsUser", SetLastError = true, CharSet = CharSet.Ansi, CallingConvention = CallingConvention.StdCall)]
public extern static bool CreateProcessAsUser(IntPtr hToken, String lpApplicationName, String lpCommandLine, ref SECURITY_ATTRIBUTES lpProcessAttributes,
ref SECURITY_ATTRIBUTES lpThreadAttributes, bool bInheritHandle, int dwCreationFlags, IntPtr lpEnvironment,
String lpCurrentDirectory, ref STARTUPINFO lpStartupInfo, out PROCESS_INFORMATION lpProcessInformation);
[DllImport("kernel32.dll")]
static extern bool ProcessIdToSessionId(uint dwProcessId, ref uint pSessionId);
[DllImport("advapi32.dll", EntryPoint = "DuplicateTokenEx")]
public extern static bool DuplicateTokenEx(IntPtr ExistingTokenHandle, uint dwDesiredAccess,
ref SECURITY_ATTRIBUTES lpThreadAttributes, int TokenType,
int ImpersonationLevel, ref IntPtr DuplicateTokenHandle);
[DllImport("kernel32.dll")]
static extern IntPtr OpenProcess(uint dwDesiredAccess, bool bInheritHandle, uint dwProcessId);
[DllImport("advapi32", SetLastError = true), SuppressUnmanagedCodeSecurityAttribute]
static extern bool OpenProcessToken(IntPtr ProcessHandle, int DesiredAccess, ref IntPtr TokenHandle);
#endregion
static private void wirteFileTest(string orgmsg)
{
string msg = DateTime.Now.ToString("yy-MM-dd(ddd) HH:mm:ss") + " : " + orgmsg;
string logfolder = AppDomain.CurrentDomain.BaseDirectory + @"\LOG\";
if (Directory.Exists(logfolder) == false)
Directory.CreateDirectory(logfolder);
string today = DateTime.Today.ToString("yyyyMMdd");
string filepath = logfolder + "Service_LOG_" + today + "-" + DateTime.Now.ToString("HH") + ".log";
if (File.Exists(filepath) == false)
{
using (StreamWriter sw = File.CreateText(filepath))
{
sw.WriteLine(msg);
}
}
else
{
using (StreamWriter sw = File.AppendText(filepath))
{
sw.WriteLine(msg);
}
}
}
/// <summary>
/// Launches the given application with full admin rights, and in addition bypasses the Vista UAC prompt
/// </summary>
/// <param name="applicationName">The name of the application to launch</param>
/// <param name="procInfo">Process information regarding the launched application that gets returned to the caller</param>
/// <returns></returns>
public static bool StartProcessAndBypassUAC(String applicationName, out PROCESS_INFORMATION procInfo)
{
uint winlogonPid = 0;
IntPtr hUserTokenDup = IntPtr.Zero, hPToken = IntPtr.Zero, hProcess = IntPtr.Zero;
procInfo = new PROCESS_INFORMATION();
// obtain the currently active session id; every logged on user in the system has a unique session id
uint dwSessionId = WTSGetActiveConsoleSessionId();
// obtain the process id of the winlogon process that is running within the currently active session
Process[] processes = Process.GetProcessesByName("winlogon");
foreach (Process p in processes)
{
if ((uint)p.SessionId == dwSessionId)
{
winlogonPid = (uint)p.Id;
}
}
// obtain a handle to the winlogon process
hProcess = OpenProcess(MAXIMUM_ALLOWED, false, winlogonPid);
// obtain a handle to the access token of the winlogon process
if (!OpenProcessToken(hProcess, TOKEN_DUPLICATE, ref hPToken))
{
CloseHandle(hProcess);
return false;
}
wirteFileTest("1");
// Security attibute structure used in DuplicateTokenEx and CreateProcessAsUser
// I would prefer to not have to use a security attribute variable and to just
// simply pass null and inherit (by default) the security attributes
// of the existing token. However, in C# structures are value types and therefore
// cannot be assigned the null value.
SECURITY_ATTRIBUTES sa = new SECURITY_ATTRIBUTES();
sa.Length = Marshal.SizeOf(sa);
// copy the access token of the winlogon process; the newly created token will be a primary token
if (!DuplicateTokenEx(hPToken, MAXIMUM_ALLOWED, ref sa, (int)SECURITY_IMPERSONATION_LEVEL.SecurityIdentification, (int)TOKEN_TYPE.TokenPrimary, ref hUserTokenDup))
{
CloseHandle(hProcess);
CloseHandle(hPToken);
return false;
}
wirteFileTest("2");
// By default CreateProcessAsUser creates a process on a non-interactive window station, meaning
// the window station has a desktop that is invisible and the process is incapable of receiving
// user input. To remedy this we set the lpDesktop parameter to indicate we want to enable user
// interaction with the new process.
STARTUPINFO si = new STARTUPINFO();
si.cb = (int)Marshal.SizeOf(si);
si.lpDesktop = @"winsta0\default"; // interactive window station parameter; basically this indicates that the process created can display a GUI on the desktop
// flags that specify the priority and creation method of the process
int dwCreationFlags = NORMAL_PRIORITY_CLASS | CREATE_NEW_CONSOLE;
// create a new process in the current user's logon session
bool result = CreateProcessAsUser(hUserTokenDup, // client's access token
null, // file to execute
applicationName, // command line
ref sa, // pointer to process SECURITY_ATTRIBUTES
ref sa, // pointer to thread SECURITY_ATTRIBUTES
false, // handles are not inheritable
dwCreationFlags, // creation flags
IntPtr.Zero, // pointer to new environment block
null, // name of current directory
ref si, // pointer to STARTUPINFO structure
out procInfo // receives information about new process
);
wirteFileTest("3");
// invalidate the handles
CloseHandle(hProcess);
CloseHandle(hPToken);
CloseHandle(hUserTokenDup);
return result; // return the result
}
}
하지만 이럼에도 불구하고, 간혹 실행이 되지 않는 경우가 있는데.. 이는
실행시키려는 프로세스가 Listen 등을 수행하는 프로세스 일경우, 아래와 같이 팝업이 뜨게 되고,
이 허용을 안하게 되면, 실행이 되지 않는다.
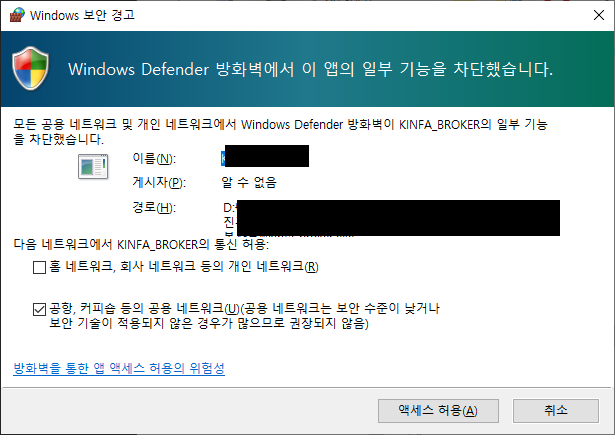
위 정보에 대한 저장은 방화벽(디펜더)쪽에 저장된다.
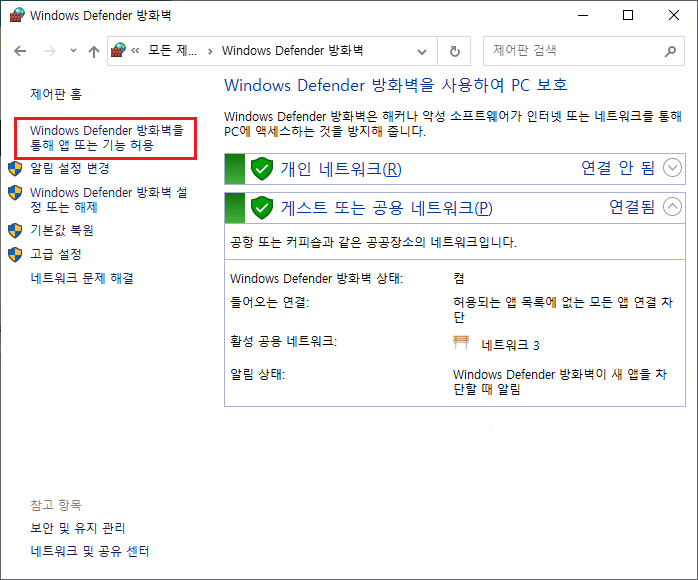
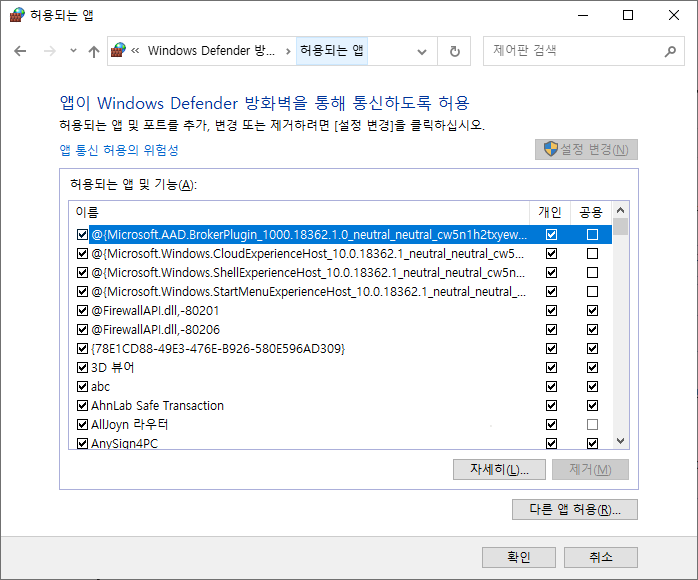
그래도 안된다면.... 윈도키 secpol (로컬보안정책) 들어가서
보안정책 - 로컬정책 - 보안옵션 들어가서
사용자계정컨트롤 관리승인모드에서 모든관리자실행옵션을 사용안함 해주어야한다
보안프로그램들이 이런 셋팅을 주로 건들지만, 저 셋팅의 기본값은
OS종류(home, pro 등)나 version 등에 따라 달라진다.
'I.T' 카테고리의 다른 글
| [Outlook] gmail ~ outlook 메일 연동시, 계속 로그인하라고 뜨는 경우... (0) | 2022.08.24 |
|---|---|
| Gmail 메일수신 알람이 안올때? (0) | 2022.07.15 |
| CPU 1 Core 1 Process 실행하기 (CPU CORE 제한하여 실행하기) (0) | 2018.03.30 |
| Win10 Visual Studio 2013, 찾기 및 바꾸기 결과 안나오 때 (0) | 2018.02.06 |
| DownMe 라는 스트리밍 동영상 다운 (1) | 2017.02.07 |





